Monday, January 11, 2010
Server Consolidation
Consolidation is a great means of cost efficiency.
Services in the past were distributed to various hosts for reliability. But systems are more reliable now; consolidating services to one box saves you hardware costs, power, cooling and most of all space (with the size of my server room I’d do anything to save space).
Especially when you need multiple machines to performing tasks which do not require dedicated hardware, virtual machines can share resources. Server are often sitting on 5% CPU utilization, there is no joy in that. And there are many incentives for a SA to use virtual machines they are quickly cloned, you can keep handy snapshots to restore the VM at anytime, machines can quickly be migrated from server to server.
With the use of a SAN a virtual cluster can be built, the virtual machine being the state of the server can reach this global file system from any hardware, in the event of a hardware failure you simply need to restore you virtual appliance to a running server, while you mend / upgrade the faulty one. On a traditional rack mounted server it would be quite a different procedure to deal with this situation.
Now you’re enabled to make the most of your hardware and you’ve greater readiness towards recoverability.
Certain hardware considerations need to be made for you to be able to make the most of your virtualization platform. Keep in mind you’re not purchasing hardware for a regular server, you’re purchasing hardware for a host server, which will share its resources amongst several guest server. All the disk and network infrastructure, the CPU cores etc will contribute to a greater performance.
Virtualization Platform
VMware’s ESX server is an excellent enterprise level server software, that can deliver great performance since it doesn’t need to be installed over an operating system, it is the operating system, hence giving you bare metal.
Microsoft is relatively new in this province and has been catching up, they only began in 2003 after they acquired Connectix.
However with the release of Hyper-V in windows server 2008 Microsoft’s virtual platform is of greater significance, without the Hyper-V the virtual machine was sitting right on top on the host operating system. Hyper-V is the layer isolating the guest operating system and at time even allowing them to interact directly with the host hardware. Though I prefer using VMware over Microsoft virtual server, the interface is much simpler and it has better support for Unix operating systems. I recently had the opportunity of using virtual server, it came free with a subscription to Microsoft’s ISV program. I was struggling to find basic features which are to easily and quickly manipulated with the use of VMware.
IIS worker processes
Worker process isolation mode is the singular greatest enhancement in IIS.
It is actually on the same lines of application isolation which Microsoft introduced with IIS 4.
If you’re new to IIS and you’re thinking …what is a worker process?
A worker process is the process in which your application’s code/ ASP application reside during execution.
Isolating worker process is in fact isolating applications, thereby increasing reliability. Lets say if one of your applications was to crash or handle memory poorly traditionally it would have effected all sites, but that’s where worker process isolation saves the day.
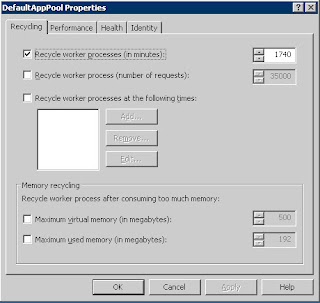
Other then that worker processes have some cool properties, by default a worker process recycles(a new worker process is initiated and takes all new requests, and the old one fades out).. anywho the default time for it to recycle is 29 hours (1740 minutes).
And you have a whole bunch of other paramaters by which you can choose to recycle it i.e by the number of requests it answers or time of day, or by the amount of memory it occupies. You can also choose to recycle them manually from the IIS console, this will not effect your site or its active users a new process takes over and old one will take no new requests and fade out.
Here’s a small screen grab from my task manager where one w3wp.exe(worker process) is taking over the other.

Here you can see the properties of a worker process (this is from IIS 6.0)
You can see the various properties/ conditions based on which the worker process would automatically recycle.
Considerations for an IT Security Policy
Considerations for a IT Security Policy
- Why do you need to have a security policy?
Geeks vs goons
In my tenure as a system admin I have encountered a good number of users, who will refuse to comply with IT policies and advice. The computers allotted to them are soon regarded as personal computers.
Such users will often install software not required for business, install an antivirus of their preference regardless of what the organisation has invested in.
Above is a win-win situation for the goons, unless you have a policy.
Without a documented policy there will be many slips and employees will use their positions and influence as they see convenient.
-How to begin
Depending on the size of your organization, you must put together a team of people who would act as a committee to jointly plan out the policy and make sure its conventional. Its best if this committee includes people of different levels of the hierarchy.
With the help of this team determine the following
- Key business infrastructure
- Identify threats to the infrastructure, identify level of risks
- Identify the access level required by departments and team members
- Identify key infrastructure to build the anatomy of your policy
- Identify privileged users
Anatomy of the Security Policy
This is the real part of your policy which will highlight the risk and mitigation plan. Which makes it the less fancy part of the document, the fancy sections would consist of -
- Overview
- Purpose
- Scope
- Policy (you are here)
- Enforcement (the hardest part)
- Version history ( be sure to mention what was revised, why and by whom)
Anywho, in the policy section you will address risks/ threats to your infrastructure and business. Mention each item against its guidelines, training, config / support details-
I’ll break the ice with few key points you need to work upon
Risk /Threat definition
You must identify what vulnerabilities exist, and which of them are actual threats.
Infrastructure /config details
Specific recommendations and configuration detail of your running infrastructure. And references to any relevant manufacturer /support documents.
Trainings and awareness
Its best if users are given basic training to know their systems better. Some basic trainings to familiarize users with antivirus software. Risks of p2p and other shareware.
Notification / escalation
Key people must be identified who would be alerted on the occurrence of a security violation. This would ideally include members of the business and tech side.
Business continuity plan / Disaster recovery plan
Altho this doesn’t entirely fit under a security document, but security procedures must leave some room for a parallel BCP /DRP effort.